L1C Signal Could Be Watermarked as Countermeasure
The U.S. Air Force will load a new signal feature, designed to make spoofing detectable, aboard a satellite that will broadcast it from space as a security overlay for the GPS L1C signal, but not until 2022 at the earliest.
The Chips Message Robust Authentication (Chimera) is now in testing under the auspices of the Air Force Research Laboratory (AFRL), getting ready to fly on the Navigation Technology Satellite 3 (NTS-3), which will trial a number of new PNT techniques and technologies.
Chimera inserts encrypted digital signatures and watermarks within the L1C signal. A GPS receiver with the requisite additional capability for this purpose can then detect whether the signal is real or fake and also authenticate the location of a GPS receiver that is remotely located.
This key feature could provide a defense against hacking by blocking access from anyone unable to prove they are at an anticipated or licensed site. Hacking, of course, is a growing threat to all sorts of infrastructure: financial, security, utility grid and more.
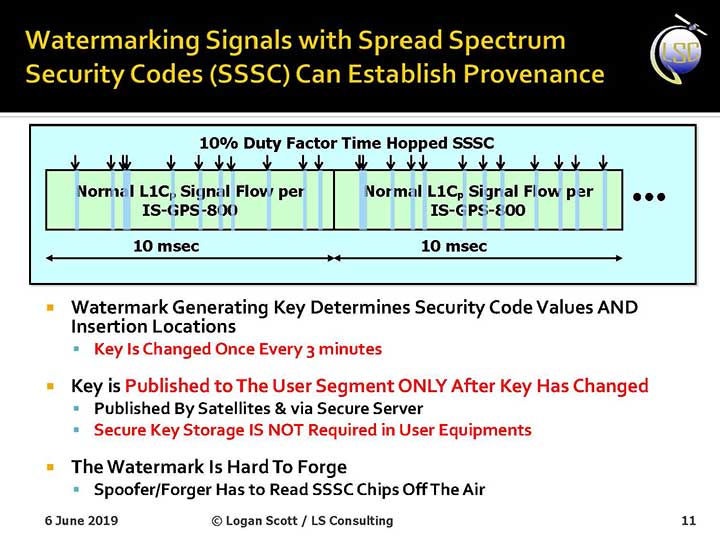
Presentation slide from PNT Advisory Board briefing by Logan Scott.
Consultant Logan Scott first proposed the Chimera technology in 2003, when he affirmed that “Some of the spoofing detection measures in wide use offer a false sense of security. Authenticatable signal architectures are needed.” In June, he made a presentation to the PNT Advisory Board: “The Role of Civil Signal Authentication in Trustable Systems.” The two slides accompanying this article appeared in that presentation.
“Chimera represents a fundamental paradigm shift in PVT security paradigms,” Scott related in a subsequent conversation. “Trust takes time and memory on a personal level and, in this case, in GNSS signals, too.
“You don’t trust somebody as soon as you meet them. Over a period of time, you get to know them. If you can’t remember anything, you can’t develop trust either.”
“In the GNSS world, there are a lot of applications where you don’t need output in real time,” Scott said. “For example, to align an inertial. The inertial provides the real-time aspect. You don’t want to send anything to the IMU that is factually incorrect. When building to aid inertial, I can afford to have a delay from real time as long as I tell it where it was 10 seconds ago. The power of that is, if I don’t have to give real-time output, I can ponder and think about things.
“If a spoofer attacks, there’s an evolution that happens there. If I, as the receiver, can see the developing scenario, and how it starts to look at little screwy, I can stop and not send anything to the IMU that might corrupt it.”
How It Works. The core concept of Chimera involves the satellites sending encrypted watermarks, encoded into the signal by the satellite. After a slight delay, the satellite sends the key used to generate those encrypted watermarks. Once a key is sent, the system changes the key.
Since the receiver has already recorded the signal with its watermarks before the key is sent, spoofers cannot know the correct key ahead of time, in time to insert correct watermarks of their own. This means that any spoofed signals can be easily spotted: either the subsequent key won’t match up with the spoofed watermarks, or there will be no watermarks at all.
“Another reason it’s hard for someone to generate these watermarks on their own is because the signal is buried below the noise,” added Scott. “The watermarks are hidden.”
A number of different time delays between signal and key are possible within this concept and within the general set-up of GPS. Scott and the AFRL have, for various practical reasons, provisionally settled on a 6-second delay on the fast watermark channel and a 3-minute delay for the slow watermark channel.
The signal enhancement could be incorporated into the Wide Area Augmentation System (WAAS). This has yet to be fully determined, but this route would lead to a faster implementation of Chimera. Scott thinks that going the WAAS route could bring Chimera capability into action within two years.
The AFRL, however, is looking at a much longer timeline. The NTS-3 satellite, where it first intends to test Chimera, will not launch until 2022 — three years hence. And that’s only a test, not an enactment or a system-wide implementation.

Slide: Logan Scott
Verification. One key benefit for commercial entities, particularly those in financial infrastructure and other systems that increasingly fall victim to hacking, is that Chimera gives them the ability to verify customers’ or partners’ locations before granting any kind of access. The customer’s or other erstwhile user’s GPS receiver would record the full signal, including the watermarks, and transmit that data to the company, entity or data center needing location verification, before the keys are published. Each combination of watermarks and signals is unique to the place where it was recorded, thus it is possible to tell whether the user is actually where they say they are, or in an authorized or pre-identified location before granting access or accepting further input (such as commands).
Scott claims that Chimera affords a 99.9% probability of detecting spoofers. “I have a 99.9% chance of detecting that the watermark is not there, because they don’t know how to generate it. This is based on how you’re processing the signal. It’s designed to be very flexible in how the receiver uses the signal.”
Just One Problem. Receiver manufacturers will have to develop new Chimera-capable receivers, and customers will have to buy them. An additional cost for the added processing, above and beyond that required for normal GPS operation, is unavoidable.
And a Hiccup. Chimera, while an acronym, is as a name perhaps not a totally felicitous choice. In Greek mythology, the chimera is a fire-breathing female monster with a lion’s head, a goat’s body, and a serpent’s tail. These historic ancestors have evolved into the word’s more current use: a thing that is hoped or wished for but that is in fact illusory or impossible to achieve.
AFRL Wants Your Opinion. The Air Force Research Laboratory seeks feedback from the PNT community on the Chimera enhancement for the L1C signal. The specification is here. And, you can download a comment form
Gilla detta:
Gilla Laddar in …